Security protocols are the tools that allow Internet and Web sites security access. The main concept is to have a safe channel that is impossible for external users to read.
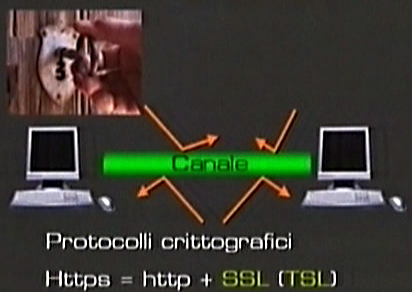
Cryptographic protocols that allow this safe channel in the Web are a variation of the HTTP protocol, that is, the protocol to access web sites. It is called HTTPS. When you link to a web site and see a small security symbol at the bottom on the right this means that the web site is made safe by using HTTPS. This is a kind of “marriage” between HTTP and SSL protocol (which has been introduced particularly to make HTTP safer). This protocol is called SecureSocketsLayer and adds some features to HTTP to make it safer. Let’s use some examples to see how HTTPS works.
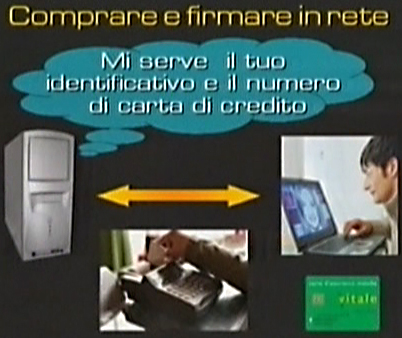
For example how can you buy and sign on-line? By using this protocol, two operations are possible. Let’s imagine I want to buy online. In order to do it I have to give my credit card number. In this operation there are two subjects involved: my PC and the server of the company that uses e-commerce.
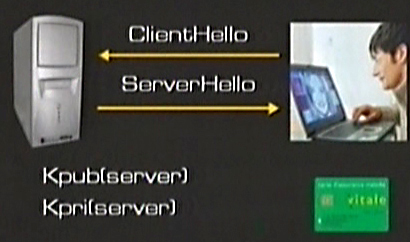
When the two computers get in touch they send each other a first message to say “ehi, look at me, I want to communicate with you by using a security protocol”. This protocol is based on the fact that the server has a public and a private key. At this point the server sends its public key to the computer that wants to connect in a safe way.
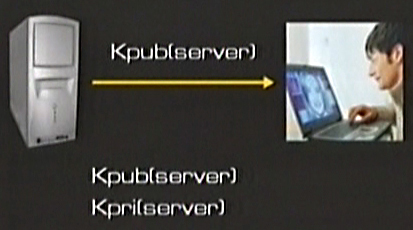
At this point what does the computer do after receiving a public key? When the browser (made safer with HTTPS) receives the public key it transmits the basic information: the credit card number. However it does not send the information clearly but coded. This means that it puts the information in the box and locks it with the public key. This box can only be open with a private key. Since the private key is owned only by the server, all the other people, even if they have the server’s public key, they cannot open the box.
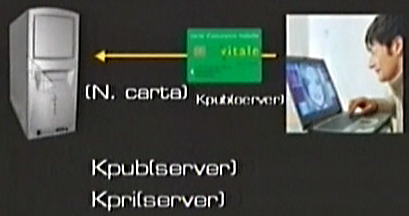
The safe box travels on the net and arrives on the server. It opens the box with the private key and reads the information related to credit card number, password or any other secret you might have.
The mechanism is based on public key distribution which can only be used to close a box and not to open it since this operation is possible only to those who have a private key that needs to be kept in the PC that is devoted to e-commerce.
This is just one of the many examples of application of cryptographic elements.