|
-- Address Spoofing
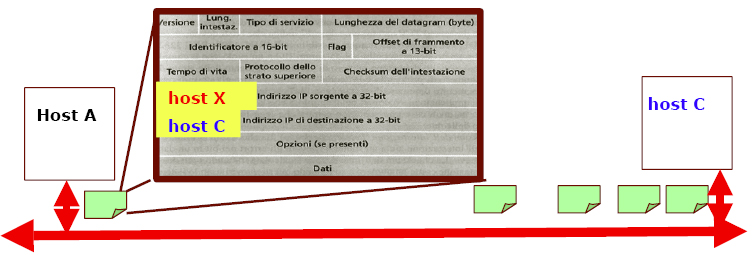
This type of attack [I1] [I2] [I3] [F1] [F2] [F3] [F4] [F5] [S1] [S2] [E1][E2] [E3] [E4] implies the falsification of the sender (Source Address) of a “datagram” (IP packet sent on the net between two nodes) to camouflage the source of the attack or to reroute the traffic between two hosts towards an intruder that will take the content of the datagram.
 19/27
19/27

|