What are the dangers of the net?
In order to have a concrete security action and to prevent it is important to know clearly all the risks. The concept of net danger a href="http://csrc.nist.gov/publications/history/ande80.pdf">[E1] is strictly related to security requirements. It can be defined dangerous every action which aims at putting in danger one of the three requirements of safe nets: privacy, availability and integrity of data. There are categories of risk for each one.
Requirement |
Category |
Type of dangers |
Privacy |
Access menace |
Communication interception, access denied, identity theft |
Availability |
Down network |
International attacks, natural disaster, environment accidents, software/hardware damage |
Integrity |
Data alteration |
Malware execution, human mistake (of the user or operator) |
Besides, when we talk about dangers in net security we have to remember that the net is often unsafe as you can see from this picture:
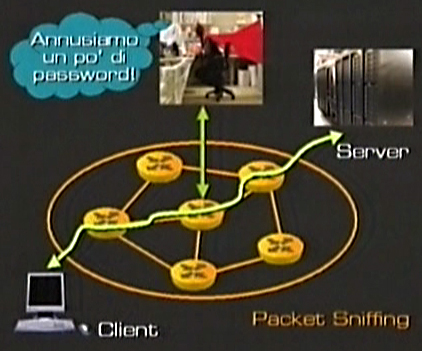
In the net there are certain information and some people may sniff packets that travel on it by using a specific type of equipment and software (that is packet sniffing). If the packets contain a password, the problem is serious and the system can result completely damaged.
The following image shows instead how sometimes ill-disposed people can pretend to be other subjects/computer.
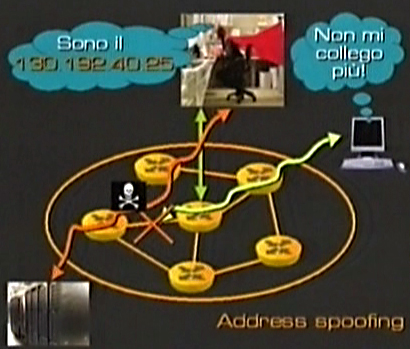
This technique is called address spoofing. The address of a computer is stolen and it is disconnected from the net and given to another computer so that the server thinks to talk to a certain subject/computer but actually is talking with somebody else. This can bring many problems.
More dangerous is the so called group attack or DenialOfService(DoS) [I1] [I2] [I3] [F1] [F2] [F3] [S1] [S2] [S3] [S4] [E1] [E2] [E3] [E4].
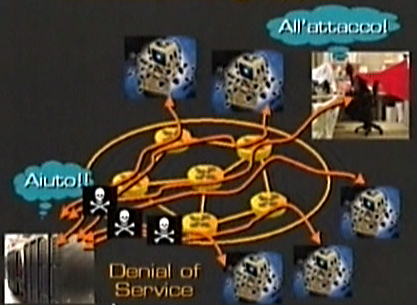
In this type of menace a hacker or an ill-disposed can, after damaging a certain number of computer and introducing deviously specific types of software, rouse an attack toward a web site for example.
He becomes a sort of “conductor” and forces other computer where he hide a software deviously to send at the same time messages to the server which receives so many messages that is not longer available to outline the functions it should do (for example to offer web pages in the case of a web server).
These are just examples but have been also quoted by mass-media as important dangers for nowadays computer science.