|
-- Secrecy
In this section we will see how to perform secrecy by using asymmetric cryptography.
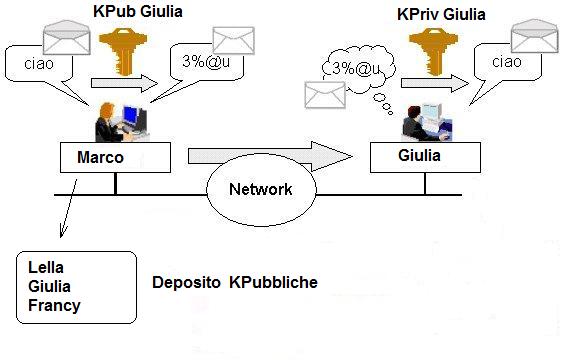
It is very easy to guarantee message secrecy by using asymmetric cryptography. In fact, unlike the symmetric cryptography, there is not the problem of sharing the key because the key used to code and decode the message are different. Let’s imagine that Marco owns Lella’s, Giulia’s and Francy’s public keys. If Marco wants to send a message to Giulia he will put the document in his box and will lock it with Giulia’s public key. At this point only Giulia’s private key will open the box. This is because of the mechanism of keys we have been talking about, in which if we close the box with a key we can only open it with the other and vice versa. If Giulia will keep her private key safely she will be the only owner and she will only open the box. This is a warranty of secrecy.
 13/27
13/27

|