Cryptography [I1] [I2] [I3] [I4] [I5] [F1] [F2] [F3] [F4] [S1] [S2] [S3] [S4] [S5] [E1] [E2] is the discipline which teaches both how to “codify” or “cipher” a message to make it incomprehensible to everybody except the addressee and how to “decode” or “decipher” a message with the secret key unknown. Cryptographic techniques are used nowadays to make communications between two users (computers) safer, so that it is not possible for a third subject to catch confidential information by intercepting what happens on the channel.
The problem of secret information, or better of transmitting secret information is as old as the human being. One of the most famous cryptography techniques can be found in Cesare’s code book. He used it during his campaigns when he had to transmit to his generals some strictly confidential information.
In Cesar’ code book each letter of the normal alphabet was replaced by the letter that was placed few positions after. In particular, Cesar used 3-step shift (the key was “3”). This was the scheme:

In order to codify the message it was sufficient to replace each letter of the normal alphabet with the correspondent letter of the “coded text”; in order to decode the process is opposite. This is a simple example:

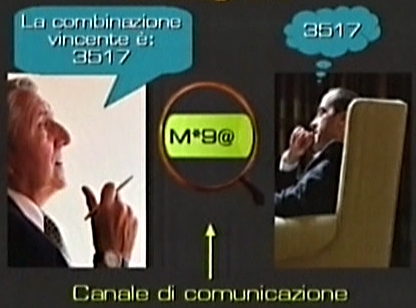
As the following image shows, the cryptography has two main aims:
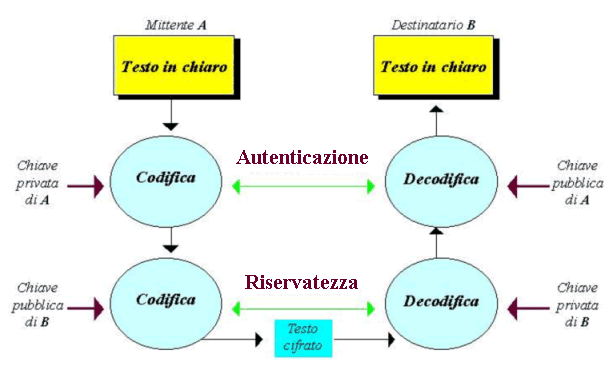
The first aim is to keep information secret. The second is the authentication, that is to say the certainty that the computer I want to link up with is exactly the one that I choose or that I assume to be my interlocutor.
In order to create these two fundamental functions there are cryptographic techniques that can be divided in two main categories. The symmetric cryptography (or with secret key) and the asymmetric cryptography (or with public key).
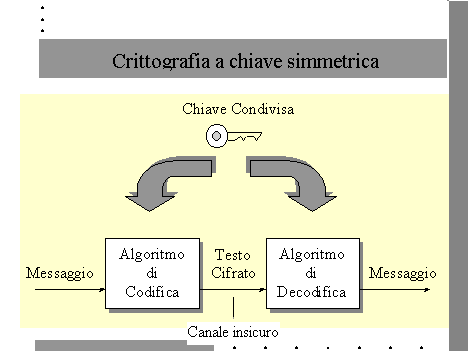
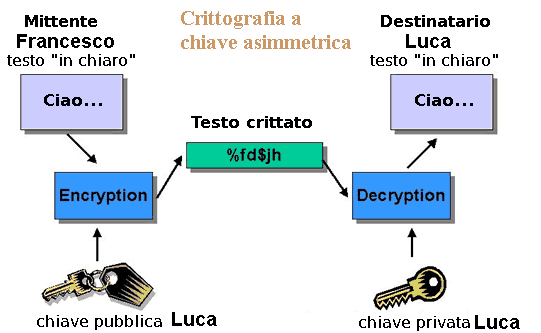
The first one basically needs one key, the second as you can see, two. But what are these keys and how do they work?

By using a metaphor the cryptography can be compared to a blender that takes the bit sequence, mixes it in a certain way so that this sequence becomes a new one and is no longer recognisable. However there must be a correlation between the initial and final sequence, otherwise we would lose information completely. The correlation between the initial bit sequence and the cryptographic sequence is determined by a key. This key opens the cocker and let us pass from a incomprehensible sequence to the initial one. Cryptography is basically a process in which we take an initial sequence of bit and we change it by using a specific algorithm. This algorithm uses a specific key that can and must change every time, and has to be secret to the majority of people. It must be known only by the sender and the addressee. Once the information has been coded by using a specific key, a new sequence is generated. It is not linked to the initial one. Then, the coded sequence is put in the blender that on the contrary brings back the initial information. If the key that allows to re-create the initial sequence is the same used to cipher the message it is called symmetric. If the key used to decode the message is different from the one used to code the initial sequence it is called asymmetric.
An important aspect to make both methods work is the choice of the length of code/decode key.